
How do you know, HTTPS is the secure version of HTTP and is used in all kinds of web applications such as Twitter, Gmail, different banking systems, etc; It allows adding a security layer to applications through encryption whose support is a certificate that allows "certifying" the identity of that entity (computer, company or person).
Private and public keys in certificates

These certificates contain a public and a private key; the public key is the one that we generate through the CSR and that is validated by another server (that would be the idea and that we do not sign the request).
The private key is simply a security password that we generate in later steps and it stays on the server and should not be shared.
In order to generate the private and public key, we will need some additional tools so that we can use HTTPS on our website, which we will see below.
Apache mod_ssl module
The mod_ssl is nothing more than a module for Apache that provides support for SSL and we must install it to be able to use HTTPS on our website.
On machines that use RPM repositories such as Fedora, we can install the Apache mod_ssl module with the following command:
yum -y install mod_sslGenerating the SSL certificate
With our module for SSL support installed, we can start generating the certificate for our site.
We open the console in linux and we locate ourselves in any directory (later we locate them in the specified path); With this we can go to the next step.
Generation of the private key
First we must create the private key that will have a length of 1024 characters (there are other parameters such as -des3 to specify a triple encryption algorithm but these are optional):
openssl genrsa -out ca.key 1024CSR generation
The CSR (certificate Signing Request) is a file that contains information about the person or company (location, domain...); with this file we can request another certified entity to sign it and in this way that the data we provide is correct and in this way a chain of certifications is put together and our entity becomes certified.
openssl req -new -key ca.key -out ca.csrWhen you execute the previous command, you will see that it requests a series of information where the most important is the one referring to the domain; sale has been our public key and is the one we must share with another server (under normal circumstances) for validation.
Self signed certificate
Although it would not be ideal for any application in production, we will self-sign the certificate and the validity period that we can set to 365 days is established:
openssl x509 -req -days 365 -in ca.csr -signkey ca.key -out ca.crtRelocate previous files
Finally, we need to relocate the previously generated files to their final location in our Apache directories:
mv ca.crt /etc/pki/tls/certs
mv ca.key /etc/pki/tls/private/ca.key
mv ca.csr /etc/pki/tls/private/ca.csrEnabling SSL in Apache
Now we need to locate the ssl.conf file which is possibly located in /etc/httpd/conf.d/ssl.conf and we need to look for the following lines:
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
SSLCertificateKeyFile /etc/pki/tls/private/localhost.keyAnd change them to:
SSLCertificateFile /etc/pki/tls/certs/ca.crt
SSLCertificateKeyFile /etc/pki/tls/private/ca.keyWe verify that Apache listens to the corresponding ports (SSL works with port 443 and port 80 is the default used by Apache) in the file /etc/httpd/conf/httpd.conf the following lines must be present and uncommented:
Listen 80
Listen 443Configuring the VirtualHost in Apache
Now we locate the file /etc/httpd/conf/httpd.conf: and add/modify the VirtualHost of the site:
<VirtualHost crm.net>
DocumentRoot /var/www/html/crm
ServerName crm.net
</VirtualHost>
We restart the apache service:
sudo service httpd stop
sudo service httpd start
Or:
service httpd restart
And if everything has gone well for us; We will see a site like the following:
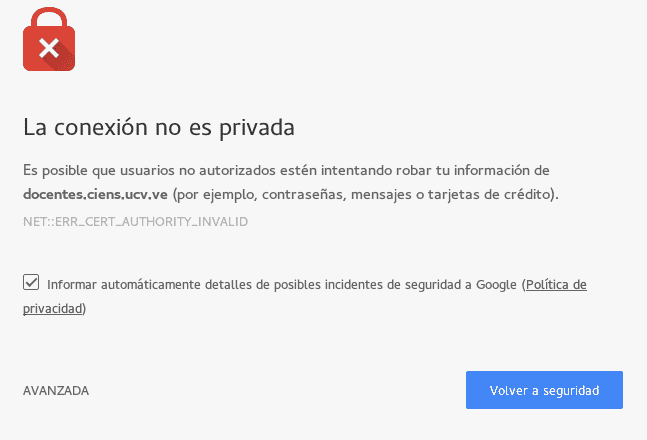
This error is due to the fact that the signature is self-generated and therefore it is considered an unreliable site.
Possible error:
If Apache does not start, we can check the apache log, in my case I checked the log located at:
gedit /var/log/httpd/ssl_error_logAnd at the end of the file there was an error like the following:
Permission denied: AH02574: Init: Can't open server private key file /etc/pki/tls/private/ca.key
This error is due to the way these files were created (outside of the Apache directory); in Linux each file has a series of information called context, depending on how this information is structured it is possible that certain processes do not execute correctly or simply deny execution (as is happening to us); We must restore the context of the files so that they can be executed, for that we must use the following command for each of the copied files:
sudo restorecon -RvF /etc/pki/tls/private sudo restorecon -RvF /etc/pki/tls/certs
You must keep in mind that the system also has the necessary permissions to run.
I agree to receive announcements of interest about this Blog.
The steps to be taken to create an SSL certificate (private and public key) and secure access via HTTPS with the Apache mod_ssl module will be explained.
